Psiphon VPN V3.183 Multilingual [Portable] Fast Connection Speed & keep You Anonymous On The Internet & Solve The Problem Access Blocked Websites & Content
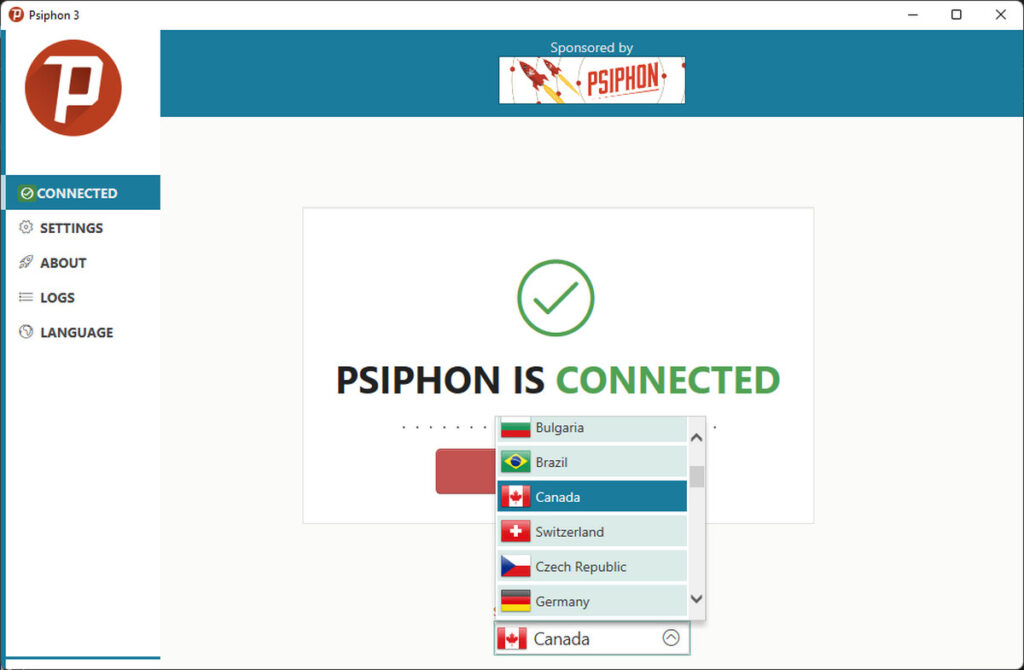
Psiphon Portable acts as a virtual private network (VPN) service that enables users to browse the internet anonymously and securely. By utilizing a combination of cutting-edge technologies, including VPN, SSH, and HTTP Proxy, Psiphon creates a secure encrypted connection between the user’s device and its servers. This connection acts as a tunnel, encrypting all internet traffic and preventing any surveillance or censorship attempts from third parties. As a result, users can freely access websites and online services that may otherwise be blocked or restricted in their geographical location.
Main Features :
- Supports SSH and SSH+ protocols for increased security.
- Manual and automatic selection of different countries of the world for connection.
- Output of reports on the work of the client.
- Detailed instructions on the home page of the program.
- A large number of connection settings.
- Hides the user’s personal data.
- Works with all modern browsers.
Overview :
The utility uses VPN, “SSH” and “HTTP” proxy technologies. “Psiphon” is the best tool for accessing the Internet and will protect you from hacked accounts and stolen passwords no matter what network you are connected to. “Psiphon” automatically ‘knows’ about new servers and thus increases your chances of circumventing censorship.
How Psiphon Works :
Psiphon Inc. has provided open access to the Internet for millions of citizens around the world since 2006. Psiphon operates a proxy system known as “Psiphon 2” as well as “Psiphon 3,” which is an application (“app”) for Android, Windows, and iOS. The following documents focus on the Psiphon 3 network, which is the most widely used. Psiphon is a free, open-source, censorship circumvention software. It uses a combination of secure communication and obfuscation technologies to allow users to connect with apps and content which would otherwise be blocked.
The internet :
The internet is a global network of billions of computers (or “routers”) which communicate with one another. These connected systems allow people to share (or “serve”) information to others. The internet can be visualized as a web, with multiple routes and connections. If one connection is severed, the redundancy of the web infrastructure allows people to connect by finding another route. To get from one location to another, web traffic (messages sent on the internet) make many hops. Traffic travels from router to router before arriving at their destination. In order to do this, specific networking and routing equipment is required. This is provided by Internet Service Providers (“ISPs”). ISPs allow internet users to use their infrastructure, including “serving” content or providing access to other content that other ISPs “serve”, usually for a fee.
Filtering and Censors :
Filtering can occur at one or many points in the network, such as, the internet backbone (often the international gateway), ISPs, institutions (such as companies or schools), and even on an individual’s device (such as a phone or desktop computer).
Censors are actors implementing filtering at any level. They could be implementing filtering on behalf of another body, such as when an ISP filters content under orders of a government.
In order to block only certain types of traffic, the traffic must first be identifiable. When a system can differentiate between types of traffic passing through the network, it is potentially able to make decisions about that traffic. Filtering can be done through devices and programs that analyze and forbid certain types of traffic to pass. In some places technical blocking affects everyday Internet use.
Circumvention Tools :
Psiphon is part of a category of technology known as circumvention tools. Circumvention tools are designed to bypass interception technical forms of blocking online. Circumvention tools usually work by either diverting web traffic so it avoids the machines that filter or by disguising the traffic to appear like traffic that is not subject to filtering. The Psiphon app does both. As filtering techniques become more sophisticated, circumvention tool providers must always update their technology and so methods and strategies are continually evolving.
Psiphon Traffic :
As a censorship circumvention tool, the Psiphon app’s primary objective is to establish a connection to the internet. The Psiphon app attempts to connect to known Psiphon servers using various methods. Sometimes the Psiphon traffic is obfuscated, meaning that it is disguised to look like a different or less identifiable type of traffic.
Because it is encrypted, censors are unable to see the content of traffic passing through the tunnel. Censors may still attempt to block encrypted traffic based on other characteristics, such as communication protocols. Communication protocols are a set of rules used to route data and ensure it arrives at the intended location.
| File Info | Details |
|---|---|
| File Name : | Psiphon_V3.183 [Portable].7z |
| Version : | V3.183 (Updated 2024) |
| File size : | 11.0 MB (ِExtracted Size : 71 MB) |
| Password RAR : | laroussigsm.net |
| Download Link : | 𝗨𝗣𝗟𝗢𝗔𝗗𝟰𝗘𝗩𝗘𝗥 | 𝗙𝗥𝗘𝗘𝗗𝗟𝗜𝗡𝗞 |
How to use it?
- First, you need to download Psiphon 3.183 [ Portable]
- Extract all files at c: drive (Most important).
- Now open the extracted file and if it is only an “PsiphonPortable.exe” then click Portable File and run it as an admin.
- Now once is ready for use simply go to the desktop and run the tool as an admin.
- One tool interface is open you can use the tool.
- Enjoy!
Take a Backup: If you are willing to try the above tool, then please take a backup of your personal data from your Android Smartphone or Tablet. As flashing any Firmware or recovery may brick the device.
Credits : The Tool is created and distributed by the developer. So, full credits go to the developer for sharing the tool for free.